Oscar-winning actress Jennifer Lawrence is known for being funny, outspoken, talented and someone you likely want to get a beer with. Unfortunately, “photo hacking victim” was added to this list of descriptors in August 2014, when pictures from her iCloud were stolen and posted online. Jennifer joined the ranks of A-list celebrities such as Kate Upton, Kaley Cuoco and Kirsten Dunst, all of whom had their personal data targeted by hackers. Incidents like these should make everyone stop and ask themselves, “How secure is my technology? Am I taking the correct steps to protect myself and my sensitive information?” Here are a few tips to shore up your security:
Know your cloud storage settings
Whether you have an iPhone or an Android, your photos may be automatically saving to the cloud. Check your settings to make sure you haven’t been opted into cloud storage without purposefully choosing to do so.
For iPhone users, go to “Settings,” then “iCloud,” then “Photos.” Within the photos tab, you’ll have the option to toggle three different iCloud photo services on or off: iCloud Photo Library, My Photo Stream and iCloud Photo Sharing. Review the description for each so you can make an informed choice about which to enable or disable.
For Android users, open the Google Photos app and tap the menu icon in the top left corner. From there, go to “Settings,” then “Back Up & Sync.” Turn off this feature if you don’t want your photos automatically backed up to your Google account.
If you discover that your phone has been saving your photos to the cloud automatically, it’s best to check what’s saved and delete anything you don’t want to be internet-accessible. You can do this by signing into your online iCloud or Google Photos account and then browsing or deleting as needed.
Know password best practices
Passwords are the frontline security for all our personal information. With that in mind, choosing to use a weak password is like choosing to close your door without locking it. Optimal – and, in our opinion, mandatory – characteristics of a strong password include:
- At least 12 characters in length
- A mix of uppercase and lowercase letters, numbers and special characters (inconvenient, yes, but ultimately safer)
- Low “guessability” (avoid pet names and birthdays – in fact, steering clear of real words altogether is your safest bet)
Not only should all your accounts have strong passwords, you should change these passwords frequently and have a different one for every account. If this sounds overwhelming, look into using a password manager to keep all your access information organized – we recommended a couple of our favorites in a recent blog post.
If you’re still not sold on the importance of strong password practices, keep this in mind: Although iCloud was initially blamed for the photo leaks afflicting Jennifer Lawrence and others, it was later determined that such attacks targeted usernames, passwords and security questions. In other words, the storage location was not to blame – rather, hackers broke into accounts by taking advantage of weak password practices.
Know (and use!) two-factor authentication
Most people hear about two-factor authentication (2FA) and think, “Not another step!” We understand the associated annoyance (we use 2FA here at MyITPros), but navigating a slightly more complex login process is a lot less inconvenient than dealing with the fallout of a cloud hack or identity theft.
Simply put, 2FA requires you to enter your username, password and an additional piece of information at login – typically a unique code generated in-app or sent via text. Because 2FA combines something you know (your password) with something you have (your phone), it’s much harder for hackers to access your account.
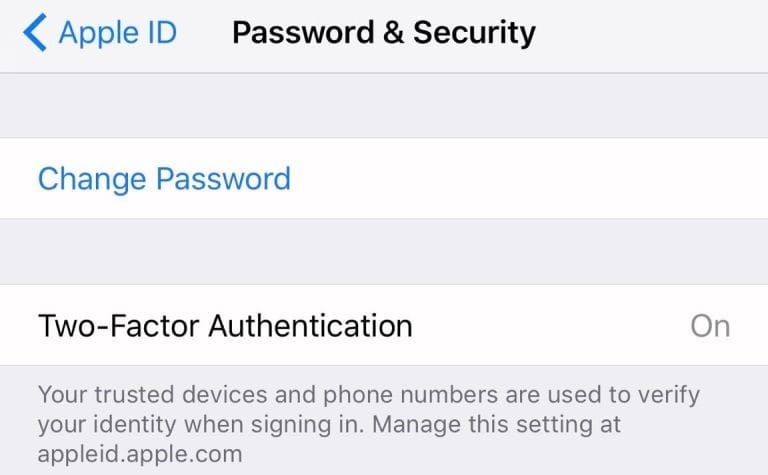
Apple device users can turn on 2FA by going to Settings – iCloud – Password & Security.
Meanwhile, Android users can check out this guide from Tech Radar.
While our hearts go out to Jennifer Lawrence and other celebrities whose privacy was compromised, their stories serve as a reminder that private information is only as secure as you make it. Although complex passwords and 2FA may seem inconvenient in the moment, they cause a lot less of a headache than being victimized by a hacker.
The purpose of this blog is to name drop celebrities- and to answer the questions you ask! To find out more about our security offerings, contact us today! You can also read up on other tech tips here!