Top 3 email fraud prevention tips for cybersecure SMBs

Given the massive threat that email represents (91% of cyberattacks start with email), in the sections below we’ll unpack some of the most common email related cybersecurity threats to remote teams. Furthermore, we’ll cover some of the simple ways you and your team can spot these attacks before they happen to your Central Texas business.
Top 3 email cybersecurity threats (and how to avoid them)
1. Phishing
While phishing has been around since well before COVID-19, the rate with which it is being deployed is at an all time high. It’s far and away the most common method for cybercriminals to breach SMBs and exploit their critical data.
Phishing is a form of email fraud that typically provides a link to a bogus website where the end user is required to enter sensitive account information. The site may ask you to provide your social security number, tax ID or bank account information or any number of sensitive data points related to the company or clients.
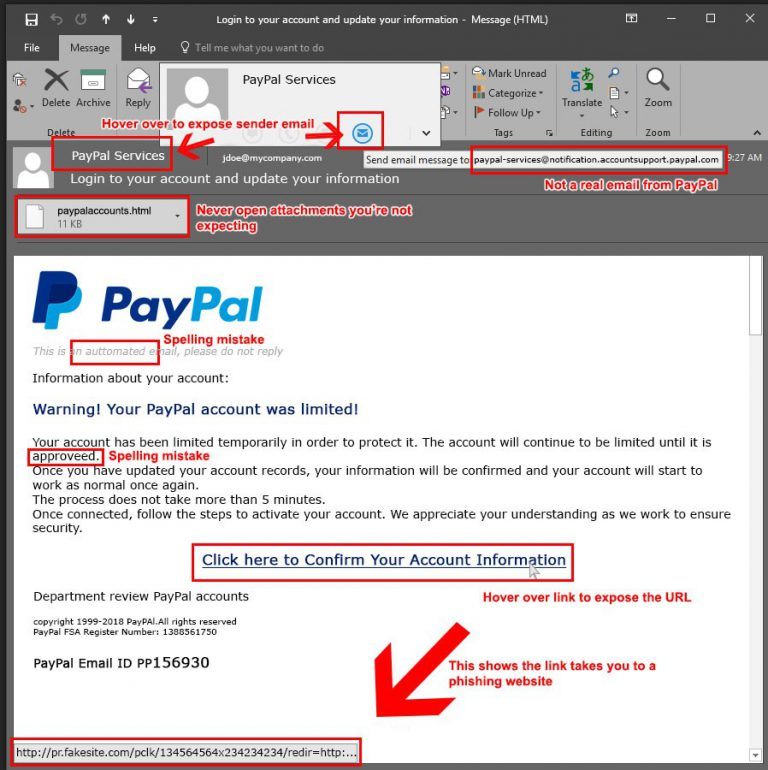
Often these emails look 100% legitimate and show up in the form of a PDF (scanned document), a UPS or FedEx tracking number, Facebook notification, bank notification etc. That’s what makes these messages so dangerous – they look exactly like a legitimate email.
So how can you tell a phishing email from a legitimate one?
How to spot a phishing attempt
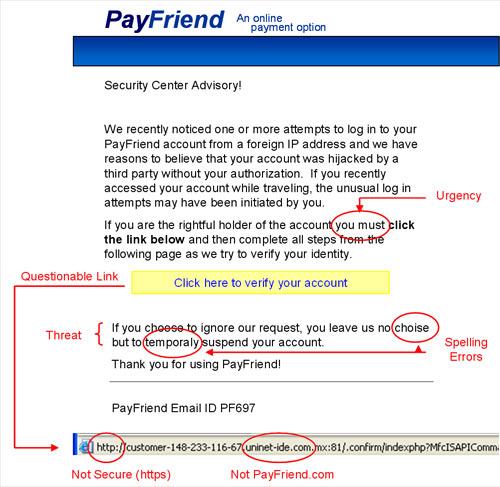
- Hover over the URL in the email (but DON’T CLICK!) to see the ACTUAL website you’ll be directed to. If there’s a mismatched or suspicious URL, delete the email immediately.
- In fact, it’s good practice to just go to the site directly (by typing it into your browser) rather than clicking on the link to get to a particular site.
- The email is asking you to “verify” or “validate” your login or is asking for personal information.
- A bank or other official institution will never ask you for your personal information.
- Finally, if the offer seems too good to be true, it probably is!
Work with your team to train them on how to spot these types of illegitimate requests. MSPs like Integris can help support ongoing training and testing to increase the awareness of the problem, as well as send fake phishing emails to users within your company to help keep your team on full alert. The end result is a team that instinctively spots and avoids the vast majority of phishing attacks.
2. Spoofing
Spoofing is another form of email fraud where the cybercriminal uses a faked (or “spoofed”) email header or IP address to fool the recipient into thinking it is legitimate. With entire teams out of the office and so much communication and collaboration being conducted via email, it’s easy to see how this type of attack has become so effective.
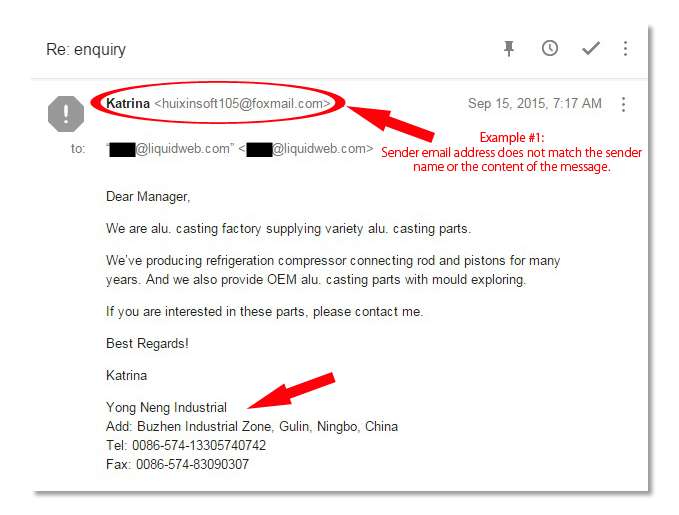
In most spoofing scams, criminals will either use the victim’s actual email account OR create a fake email account resembling the victim’s email account by adding, changing or deleting one or more characters. They pose as someone that you would actually be interacting with on a regular basis in order to get you to take their desired action.
For example:
- Legitimate email address: jane-doe@abc.com
- Fraudulent email address: jane_doe@abc.com
This could be sharing sensitive data, login credentials or clicking on a malicious link. In most cases, a spoofing link executes a malicious file that damages your operating system and critical applications while it propagates throughout your network, placing your colleagues, clients and vendors at risk.
Additionally, in many cases, malware is often downloaded to your system’s hardware, which makes it undetectable from antivirus or other security software installed.
Spoofing can also be perpetrated via an official-looking email from an important service provider that instructs you to take precautionary actions to protect your finances or reputation.The professional graphic elements used by scammers convince the email recipient that an impending threat can be suppressed by following the sender’s instructions, which usually entail clicking on a link in the message.
How to spot spoofing
If you or your team ever receive an email that appears to be from a colleague, vendor, or legitimate business contact but is soliciting goods or encouraging you to follow a link, you probably have been the target of spoofing. In such cases, the perpetrator has managed to gain access to someone’s address book.
You know the people in your network well enough to understand when something that they are requesting via email looks fishy. If all the sudden a contact is asking you to do something they normally wouldn’t, double check the sender’s email address to make sure it’s their legitimate email address.
It’s important to note that there is a difference between the email name and the display name that you see when opening emails. For example, you can make a Gmail account and make the display name for that Gmail account look like an email address for virtually any company. For that reason, when you check the address, be sure to check the actual address rather than just looking at the “from” field.
Even if it checks out, take the time to get on the phone with them first to confirm they are indeed the one making the request. A simple phone call could keep your company from a devastating breach of financial loss.
3. The “Bait and Switch”
By this point, you should be starting to see a theme as to how cybercriminals are exploiting employees who are working from home. Most of the vulnerabilities that they are exploiting have to do with the fact that people are out of the office and therefore cannot confirm the legitimacy of an email for the request contained within as easily.
The bait and switch is another form of email fraud in which the criminal actually gains access to the victims email system and can see incoming and outgoing messages. They simply wait for the opportunity to make a request and the worst part is that these requests are coming from a legitimate email address in this case.
This is especially prevalent in industries where wiring money is common and, unfortunately, is the reason that these types of attacks are currently the leading cause of wire fraud.
Here’s how the crime is typically executed:
- A criminal gains entry into the computer system and email.
- Attacker lurks in the background, reading incoming and outgoing emails. We call him “The Man in the Middle.”
- When the legitimate parties have acquired the necessary documents (usually closing instructions or wiring information), this is when he strikes.
- The “Man in the Middle” then sends “corrected” wire instructions, or alters the existing wiring instructions (i.e. bank account information and/or beneficiary) for the purpose of diverting funds to a bank account under their control.
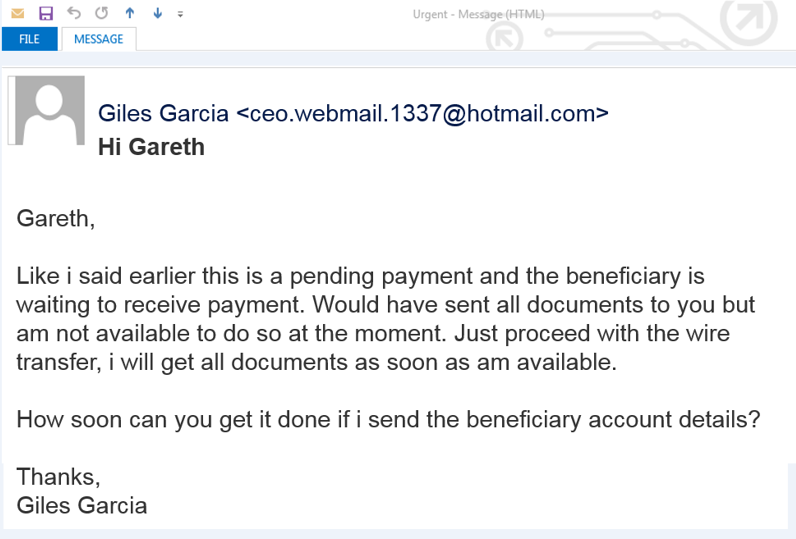
Emails will be sent from addresses that appear to be similar or identical to the original, with minor changes like…
mdombrowski@suntitleagencey.com
mdombrowski@suntitIeagency.com
Can you spot the difference?
By sending the transfer to an account with the minor change the wire ends up in the hands of the criminals and the victim is out the entire balance of the transfer.
Avoiding email fraud for your remote or hybrid remote workforce
A whopping 95% of cybercrime is caused by human error and the majority of that error is related to cybercriminals manipulating well-meaning employees with fraudulent emails. By educating your team on what to look for, what actions to take when they suspect fraud and setting clear work from home policies about how to use their technology, you’ll be able to dramatically reduce your vulnerability.
Unfortunately, not everything can be solved with awareness training and cybersecurity policies. There are still changes that need to be implemented to your hardware, software, network and policies as a whole in order to further reduce your risk. Contact the cybersecurity experts at MyITpros to evaluate your company’s vulnerability and help you take the steps necessary to remain protected against devastating breaches.