Responsible IT Architecture
Responsible IT Architecture for your business
It helps us create safe, future-focused, and fully optimized IT systems for our clients. At Integris, Responsible IT Architecture is the term we use to describe our goal and purpose.
Think of it as a comprehensive plan for the safety and efficiency of your systems. Like a seatbelt for your car, a Responsible IT Architecture runs quietly and reliably in the background, offering critical protection, wherever you go.
So how, exactly, do we create a Responsible IT Architecture for our clients?
- By setting a standard based on cybersecurity guidelines set by the National Institutes of Science and Technology (NIST), industry regulators, and cyber risk insurers
- By providing a suite of backup and cybersecurity tools that, when used together, create a powerful wall of protection for your company.
- And by using the Responsible IT Architecture standards to guide monitoring, reporting, and IT policy for your organization.
Responsible IT Architecture truly is at the heart of everything we do at Integris. When you sign on for our fully managed IT programs like Empower or Empower+, we’ll start by doing a thorough assessment and gap analysis of your organization, to see what parts of your systems need to be upgraded to meet Responsible IT standards. The implementation plans we write for you will help you ramp up to a whole new level of systems performance, quickly.
When you have a Responsible IT Architecture, you’ll get tremendous business benefits, and an IT foundation that can help you:
- Protect your networks with firewalls and hack-resistant authentication
- Create a bulletproof platform that protects you against outages, disasters, and data loss
- Continuously patch, monitor, and remediate vulnerabilities in your system
- Filter out bad actors and code trying to interact with your systems
What can a Responsible IT Architecture do for your company?
- What could your business accomplish if your systems were built on the right foundations? Plenty. When you work with Integris, we take on all your daily IT headaches, so you can focus on getting down to business.
- Let Integris manage your IT vendors, so you’ll never have to juggle multiple accounts, data sets and dashboards again
- Stay one step ahead of your compliance requirements for regulators and cyber insurers
- Ensure that your systems are up to your usage requirements, eliminating traffic-based outages and bottlenecks
- Never lose data, with cloud backup that never runs out or goes dark
- Prove to customers and clients that their data is safe when it’s in your hands, with cybersecurity documentation that wins you business
Breaking it down: Responsible IT Architecture pillars
Our Responsible IT Architecture stack is designed to work together to create the ideal defense for your systems. Each one of these tools has its own job to do, each reinforcing the other. When you sign up for our Empower managed service plans, we’ll ensure your company has the industry gold standard for:
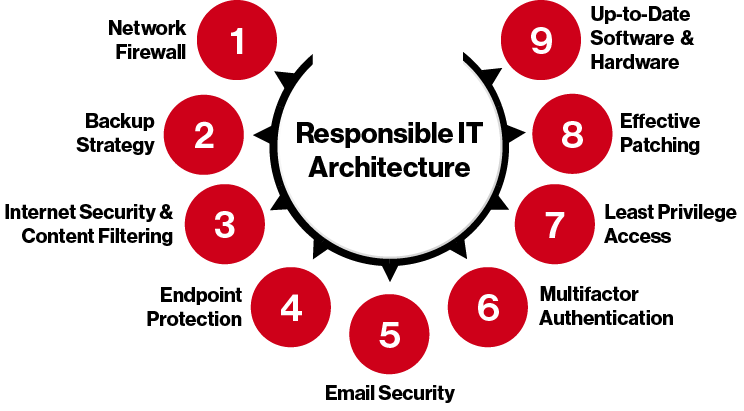
Network Firewall
At Integris, we take firewalls one step further, offering our clients a firewall paired with 24/7 monitoring and local, onsite service. You’ll get all the installation, maintenance, logging, and replacement services you need to safely integrate our firewall into your company’s defenses.
With our advanced firewall product, we’ll do onsite installations and networking, and once it’s installed, have 24/7 monitoring and help desk assistance, continuous assessment and patching, and a dedicated vCIO that handles documentation, project management and systems strategy. And of course, backup for your firewall will be incorporated into your backup and disaster recovery.
Backup strategy
With the right combination of data backup products, Integris can help your network get up and running again fast. Our data backup and recovery solutions protect your devices, your software, your files, and your operating systems. Depending on your risk tolerance, we have solutions that can backup in near real time, several times a day, or once a day. Your recovery speed can be tailored to your business needs as well. It all depends upon your budget and needs.
Internet security and content filtering
Stop your staff—before they click on that bad link—with an advanced email filtering tool from Integris. This advanced DNS filtering tool catches and filters out links that are broken/unsecured, from the dark web, or on a watch list of known bad actors on the internet.
This highly customizable tool allows you to set levels of filtering by function or location, create an unlimited number of custom block/allow lists, and more. This product can be the centerpiece of enforcement for your company’s acceptable use policies.
Endpoint protection
Every device logged into your system is a potential entry point for a hacker. This advanced security tool from Integris can help ensure the activity coming from those devices is secured. Using data analytics techniques and contextual information, this tool blocks malicious activity and provides remediation suggestions to restore affected systems. This automated detection system covers even the farthest edges of your environment. It’s a key tool for companies with a high population of remote workers, traveling workers, or a bring-your-own-device policy.
Email security
Statistics show, most data breaches start with bad links, clicked in emails coming to your employees. With an advanced email security system, you’ll be able to quarantine suspicious emails before they show up in your inboxes. Our always on, 24/7 monitoring tool uses AI-assisted technology to quickly identify suspicious emails. We offer you a safe space to evaluate, log, and report on the bad links coming through your system. Our white-glove installation and maintenance program makes running your email security system easy, and the advanced reporting is perfect for submitting to cyber risk insurers or regulators.
Multifactor authentication (MFA)
Responsible IT infrastructure begins with protecting your system’s “front door” from hackers. Multi-factor authentication ensures that you’re not inviting them in. With our MFA system, we’ll manage all the user authentications on your networks and platforms with not just one factor, but two. After submitting their name and password, users will be prompted with a push notification, usually to a separate mobile device, which allows them to verify their identity again.
This simple action foils nearly every hacker attempting to use your employee’s stolen network credentials. It’s considered a standard cybersecurity requirement for most companies—because it works. And best of all, with Integris, we’ll manage all the details for you, setting up, managing, monitoring, and servicing your accounts.
Least privilege access
Least privilege access is a permissions philosophy that ensures that only people who need the information see the information. Carefully layering permissions throughout your organization is key, as is developing a zero-trust architecture that continuously verifies the identity of the people on your systems.
Effective patching
Juggling updates and patch alerts for all your programs and platforms can be one of the most time-consuming tasks for any IT operation. Keeping track of those patches for reports is even worse. With our white glove service, you’ll never have to worry about missing a patch again. Your systems are monitored and patched 24/7, and reports are available on demand for cyber risk insurers and regulators, as well.
Up-to-date software and hardware
Legacy platform issues. Lack of budget for new programs or hardware upgrades. There are many reasons why your company may have elected not to get the latest software or hardware. While we always strive to do what’s in a company’s best budgetary interest, we do ask that all our clients get rid of programs or devices that are too old to be covered by a manufacturer’s warrantee.
When elements of your systems are no longer covered, they are often impossible to update and even harder to repair. To ensure your system’s health, we regularly review all your system assets, and make replacement recommendations that are part of your IT budget and infrastructure plan.
We start with an assessment
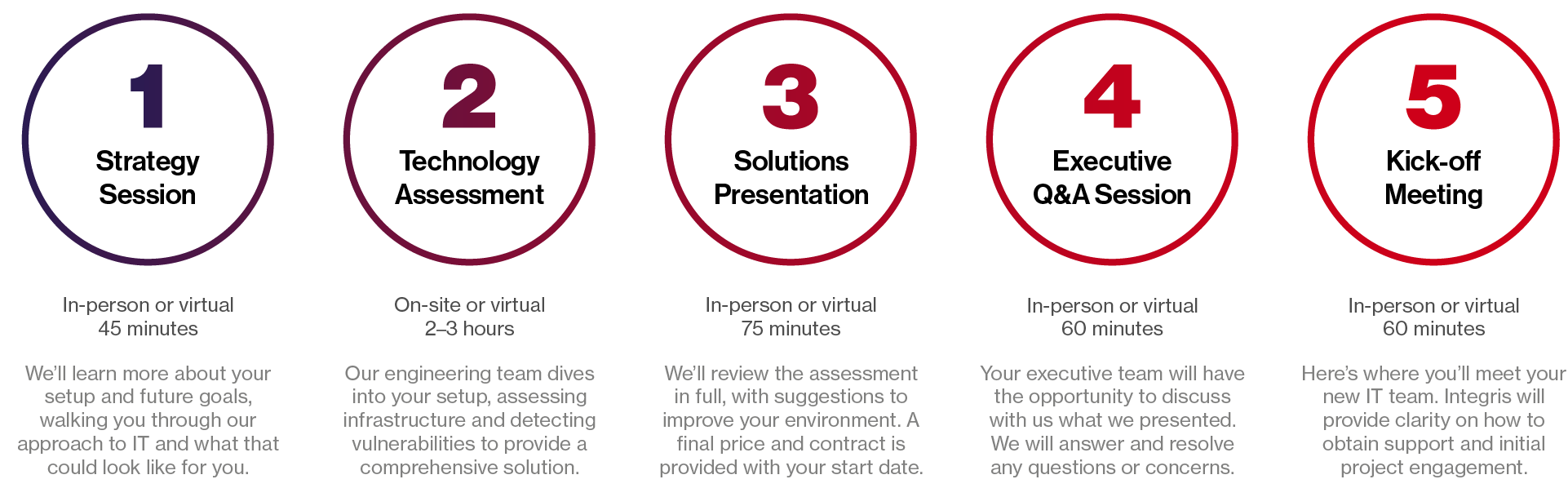
To become an Empower client, we require a paid assessment as part of our consultation process. Why? Because we believe it’s the best way to ensure that the work we do for you is focused, economical, and effective.
Our assessment looks at all areas of your IT infrastructure, from your physical network, through your software/hardware assets, to your policies and partnerships. At the end of the process, we will have completed a gap analysis, a remediation plan, and set an infrastructure roadmap and budget for the year. We’ll help you set goals, and achieve them, so you can take your business to the next level.
At the end of the assessment process, you’ll have a thorough gap analysis, an IT infrastructure implementation plan, and a budget. With this information in hand, our team can hit the ground running, and keep your systems and spend on track, right away.
What our assessments cover
During our assessment process, engineers will visit your facility with an eye to answering these questions:
- Is your network infrastructure/power supply/server space adequate for your current and future needs?
- Are there any gaps in your firewall coverage?
- Are all your endpoints effectively secured?
- How well do your cybersecurity tools, systems and policies adhere to a Responsible IT Architecture?
- Do you currently have the cloud backup capacity for a proper disaster recovery?
- What is your current patch management strategy? Are patches being done quickly enough?
- How does your company handle lifecycle management for your hardware? Do you currently have software or hardware that’s currently out of manufacturer warranty?
- Has your staff been trained on how to avoid cybersecurity threats?
At the end of the process, you’ll have a thorough gap analysis and a written infrastructure plan for your business.
What clients have to say about Responsible IT Architecture
“We have improved our security and flexibility, begun our cloud migration, and switched to remote working due to the COVID crisis. Again, with the guidance of Integris not missing a single step. Our future is planning for better efficiencies and reducing costs – all while preparing for the next unexpected turn. As Integris has proven repeatedly, Integris will be a trusted partner on this journey forward.”

Bryan LeBlanc
CIO
Pace Claims
Lead the way with Responsible IT Infrastructure that empowers your business
Interested in knowing more? We’d love to work with you. Contact us today for a free consultation.
