EDR vs. ITDR vs. MDR vs. XDR: Which endpoint security systems should you choose for your company

In the world of cybersecurity, one rule rings true: If you control the endpoints/devices that link to your systems, you’re well on your way to controlling your cybersecurity risk.
In fact, according to IBM’s 2024 Cost of a Data Breach Report, 90% of successful cyberattacks and 70% of successful data breaches originate at endpoint devices. With a risk spread like that, endpoint security tools are definitely one of the most important strategies in your cybersecurity defenses.
Unfortunately, finding the right endpoint security tool isn’t always so simple. Acronyms abound, and the differences between Endpoint Detection and Response (EDR) tools, Identity Threat Detection and Response (ITDR), Managed Detection and Response (MDR) tools, and Extended Detection and Response (XDR) tools are too nuanced and too important to ignore. Understanding the arguments around EDR vs. ITDR vs. MDR vs. XDR will be critical to your cybersecurity strategy.
At Integris, we sell all these options, and we pride ourselves on matching our customers with the right endpoint security tool at the right time. Let’s dig deeper into the differences between these three endpoint security options, so you can shop smart for these tools.
EDR vs. ITDR vs. MDR vs. XDR: What’s the difference?
All these tools do one central thing: they monitor the devices within your networks and identities for unusual activity that could indicate the presence of malware, viruses, or ransomware attacks. However, different tools cover different types of devices and services and offer different levels of service and response.
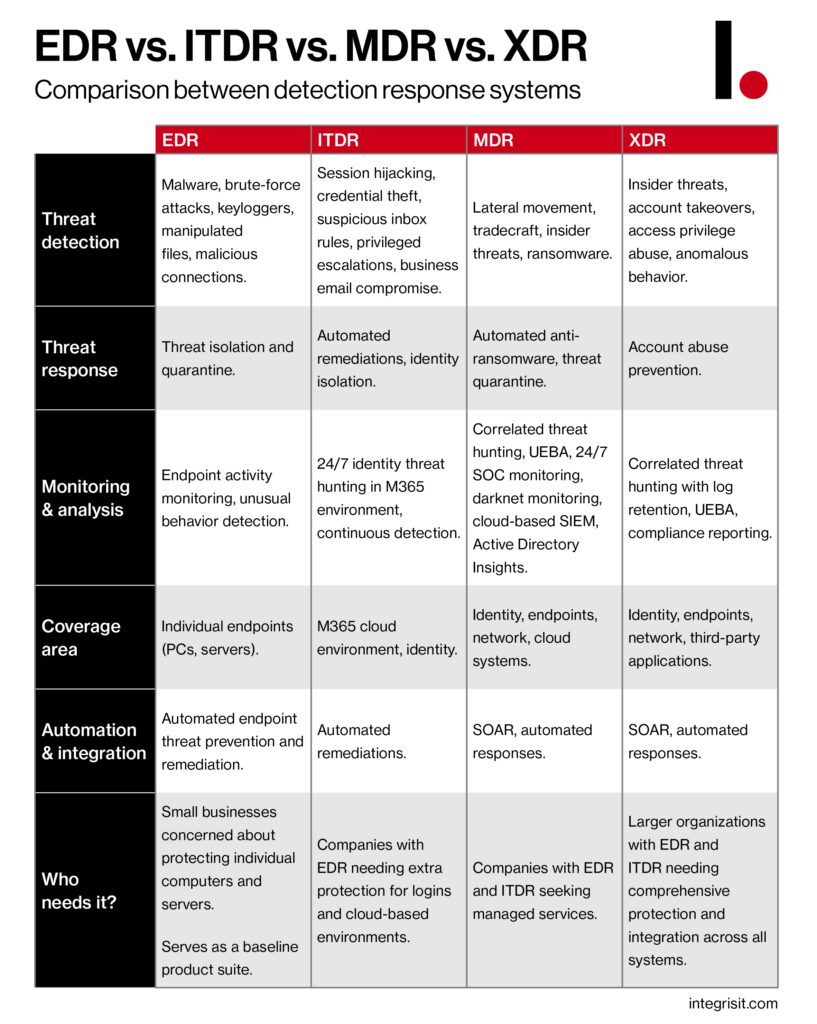
Check out our handy infographic (and download a high-def PDF of it here) and then read on for all the details.

What is Endpoint Detection and Response (EDR)?
EDR focuses on monitoring and protecting individual endpoints, such as computers, servers, and mobile devices, from cyber threats. It provides real-time visibility, automated threat detection, and response capabilities. It analyzes user behavior to weed out potential threats. When one’s found, depending on the severity, it can be quarantined until it can be properly analyzed. This tool usually also includes forensic analysis reporting of threats, so you can understand the patterns in your incoming threats. We consider this a baseline security tool that every organization should have, regardless of their size.
Pros of EDR:
Cost – As a simpler system, it’s generally the lowest cost option. If your system is smaller in scope, it will cover exactly what you need.
Scalability – It’s easy to move up to more comprehensive tools when your system demands expand.
Cons of EDR:
Remediation – While the system can quarantine, flag, and analyze anomalies, many EDR tools may require that your IT team manage remediations. This could be an issue for small IT departments without the resources to handle the flurry of notifications coming in.
Narrow scope – If your systems have associated server rooms or other tech assets beyond standard workstations, EDR alone may not offer the kind of coverage you need.
What is Identity Threat Detection and Response (ITDR)?
We also consider ITDR to be a required, “baseline” security tool, because it monitors your Microsoft M365 cloud environment. Specifically, it is a 24/7 managed Identity threat detection and response solution that protects M365 from email compromise, VPN misuse, token/session theft and unauthorized access. ITDR offers proactive, advanced threat detection to stop attacks before they happen. ITDR packages can vary but the best ones will include a combination of human and machine intelligence, to focus efforts and reduce false positives. You should also look for packages that include full remediation and guidance as well, to ensure vulnerabilities are handled immediately.
ITDR is the right tool for companies that:
- Use Microsoft authentication services for Azure Joined workstations
- Use Microsoft as their email provider
- Have compliance and security regulation requirements
- Use existing EDR programs
These days, most companies have a dispersed workforce that’s working in M365. ITDR provides a critical extra layer of security that’s not always covered in EDR packages. If that’s you, and ITDR isn’t already part of your detection and response package, it’s definitely time to add it on.
Pros and cons of ITDR:
There really aren’t any cons to ITDR, other than the extra cost of adding the tool. As for cons, I don’t see much of a downside. Everyone needs this functionality. Check your existing detection and response suite, and make sure it has an enhanced identity and cloud detection response capabilities.
What is Managed Detection and Response (MDR)?
MDR does everything that EDR does, but it adds a level of live, staffed monitoring and remediation. It includes continuous monitoring, threat detection, and rapid incident response, usually provided by a dedicated Security Operations Center (SOC).
Pros of MDR:
Cost savings of outside expertise over the long term – With a managed service product you offload the management of this tool, saving your internal team from a heavy administrative load.
Enhanced governance – The extra monitoring, remediation, and analysis you get with MDR is a great choice for smaller companies with a simple system, yet a high need for regulatory compliance and governance. If your company regularly is called up on to provide cybersecurity documentation for regulators or cyber risk insurers, MDR can take a large part of that burden off your hands.
Cons of MDR:
Extra cost of the tool– While we believe the long-term benefits of MDR are well worth it, the step up in services will generally mean an extra investment. You’ll need to analyze whether that investment is needed, based on your regulatory and system requirements.
Limited scope – MDR is generally not the best choice for larger companies with a complex endpoint network. If you have advanced factory equipment, or larger server rooms, for instance, you will most likely need to level up to an XDR system.
What is Extended Detection and Response (XDR)?
XDR takes it a step further by integrating multiple security tools and data sources into a unified platform. XDR enhances threat detection and response across an organization’s entire digital environment. This can include endpoints, networks, telemetry, firewalls and cloud services. This integrated approach is particularly beneficial for larger organizations with complex IT environments that require a holistic security solution. This is considered the “gold standard” of detection and response tools, offering the widest range of services and reporting options.
Pros of XDR:
Holistic, expert approach – Because this tool covers your whole system, it eliminates many of the bottlenecks and incompatibilities that come from having multiple monitoring tools. The extra investment you make in a dedicated 24/7 service team ensures continuity and responsiveness.
Correlated reporting – Since endpoint, online identity, network devices, firewalls, and more are all being analyzed as a whole, the SOC can detect potential anomalous activity or identity threats as they move throughout disparate systems and locations.
Unified reporting – One source of truth exists for your entire detection and response system, so patterns are easier to recognize early. A unified dashboard makes it easy to keep a high-level view of your infrastructure.
Covers advanced needs – There’s no worry you’ll grow out an XDR system, as it’s the most advanced and comprehensive type of managed detection program. This is great for a large or fast-growing organization with lots of assets.
Cons of XDR:
The costliest option – You get a lot for an XDR program, but you pay for that white-glove service. If your company is smaller, one of the other options may be a better choice.
EDR vs. ITDR vs. MDR vs. XDR: How to know what tools are right for you
It’s easy to get confused when you compare these tools, because at first glance, they seem to overlap. In reality, they each have very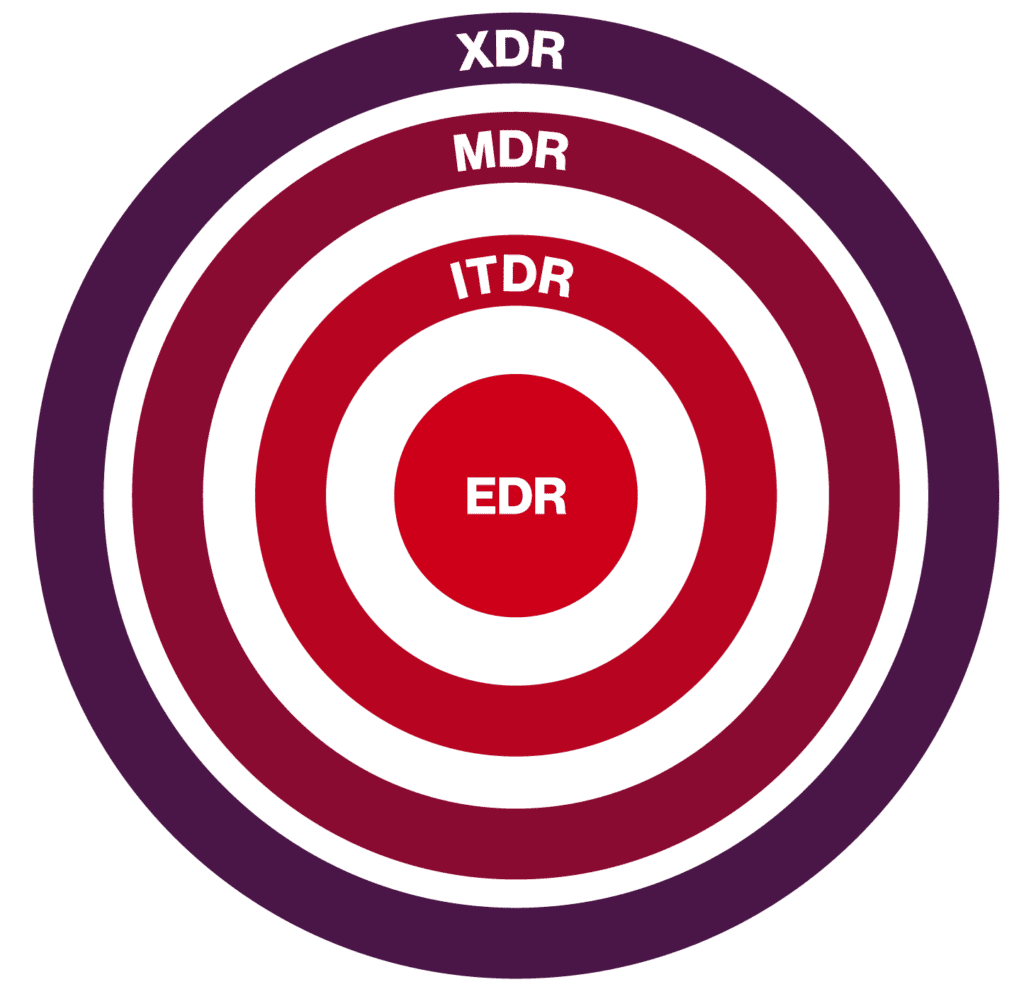 specific roles to play in your cybersecurity defenses. Now that I’ve had a chance to describe what these tools do, let me break down my opinion on what kinds of companies should invest in which of these tools.
specific roles to play in your cybersecurity defenses. Now that I’ve had a chance to describe what these tools do, let me break down my opinion on what kinds of companies should invest in which of these tools.
At minimum, every company should have EDR. Companies working in M365 should have EDR and ITDR as their baseline. These two tools fit together nicely and together represent what the baseline should be for your detection and response systems. This should be all smaller companies, or companies with a simple IT infrastructure, should need.
However, as your systems become more complex and distributed, you should invest in the additional services MDR or XDR can offer. It pays to have a cybersecurity consultant, like a vCISO, or your MSP help you evaluate which of these choices make the most sense for your company. There are many nuances that need to be considered in your current risk profile, and you’ll want to think through what your growth trajectory is likely to be in the future.
To help you understand what these tools include and how we assess need for these services, check out this chart (and you can download a PDF of it here).
Interested in exploring EDR, ITDR, MDR, or XDR for your company? Integris can help
At Integris, we offer all four levels of detection and response tools for companies across the nation. We’d love to help you find the right customized tool for you. Contact us now for a free consultation.