What is Endpoint Protection?
Also called Endpoint Detection Response (EDR), Endpoint Protection programs protect each of the devices on your network, consistently monitoring and neutralizing the cybersecurity threats that attack them. With employees logging into the network from anywhere, this critical, advanced cybersecurity tool ensures that things like phones, tablets, and laptops signing into your system aren’t endangering your networks.


How does Endpoint Protection Work?
Your organization has an enormous variety of devices that connect to your systems. Any one of them could be an easy point of entry for hackers.
Our advanced EDR tool neutralizes the threats of malware, brute-force hacks, keyloggers, and more. How? By harnessing the power of machine learning. Our system maps the patterns of each user’s normal behavior on your systems. When something’s amiss, we catch it—fast.
Our always-on technology can quickly detect manipulated files, unusual activity, and malicious connections coming from your endpoints, then quarantine them to be addressed in a safe environment. When a threat is detected, it is sent to a cloud based location off network, so it can be analyzed without endangering your systems.
The benefits of getting Endpoint Protection through Integris
We don’t just plug in a tool, and let it do all the work. Whether you work with us as a fully managed service client, or whether you order this tool a la carte, you’ll get the full benefit of our white-glove, turnkey service. With Integris, you get:
Convenient monthly billing by user
Three service options, scalable based on your needs
Coverage for all your on-site and remote endpoints, including BYOD devices
Bluetooth and firewall control available
Full-context threat storylines and custom-automated detection rule sets available
On-demand reporting
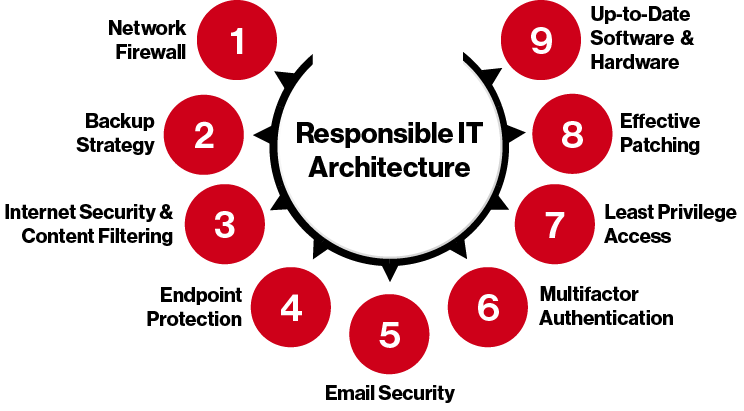
Endpoint Protection is part of a Responsible IT Architecture
There are nine tools that we use at Integris to help us ensure that the standards of a Responsible IT Architecture are met, and Endpoint Protection is one of them.
When you work with us, we prefer to take a holistic security approach. For us, that means employing these nine pillar tools, working in tandem, to create a complete layer of protection around your systems. Whether all those tools come from us, or they are existing tools in your network, it’s important that they are updated, up to the standards of regulators/cyber insurers, and up to the security demands of your network.
We’ll work with you to set up Endpoint Protection that works for you, and works together with your other security tools to keep your company safe.
Learn more about Integris Endpoint Protection
Microsoft Invests Big with New Threat Hunting Services
Microsoft is going in big on cybersecurity. Now, we’re seeing one of the first results of this investment: Microsoft Defender.
Do I Need To Improve My Endpoint Protection?
We review some of the signs that you may need to improve or upgrade your Endpoint Protection system.



