What is Least Privilege Access?
Least privilege access is more of a cybersecurity philosophy than it is an actual cybersecurity product. And this philosophy is strikingly simple.
When your company employs least privilege access, you’re being purposeful about how you distribute your system permissions. Employees, vendors, and customers are only given access to the software, storage, and permissions that they need to use. Admin privileges, in general, only go to senior IT leadership under a least-privilege access structure.
At Integris, we strongly recommend this strategy for all our clients and consider it an important part of having a Responsible IT Architecture. Why is it so important? Let’s get into the practical benefits.

Why every company should have Least Privilege Access
The primary benefit of least privilege access is obvious. The fewer people that have access to sensitive data, the lower the likelihood that data will be breached. Of course, there are a significant number of “inside job” data theft cases carried out by people with administrative access. But a data breach doesn’t have to be an active case of theft to be damaging. Often, employees may have malware in their systems they don’t know about. If that malware has a key logger attached, a hacker can have access to your most sensitive information in minutes.
Nearly every company has some type of sensitive data to protect. Perhaps it’s financial or health care data. Employee passwords and logins. Order and inventory systems. The opportunities for disruption are numerous.
When you are purposeful about creating a least privileged access system, there are written protocols for all levels of information access. Least access policies that are written down and well enforced offer the following benefits for your company:
- Faster onboarding and offboarding of employees, because their system access levels are pre-determined, and offboarding security policies are well established
- The ability to comply with the cyber security guidelines required by your cyber risk insurers, who are looking for proof your company data is being handled responsibly
- A fair and equitable system of granting access, that employees understand, eliminating conflicts
- Proof to regulators, customers, and potential clients that you take the handling of company data seriously and are complying with industry best practices for your IT

How does Least Privilege Access relate to Zero Trust Architecture?
Zero trust architecture is a way of enforcing least privilege access. Working together with tools like multifactor authentication, zero trust systems continuously verify your users’ location and credentials throughout their on-system experiences. This not only provides an extra layer of protection, it also provides an activity trail for every person in your system. This can be invaluable forensic information to have when security incidents occur.
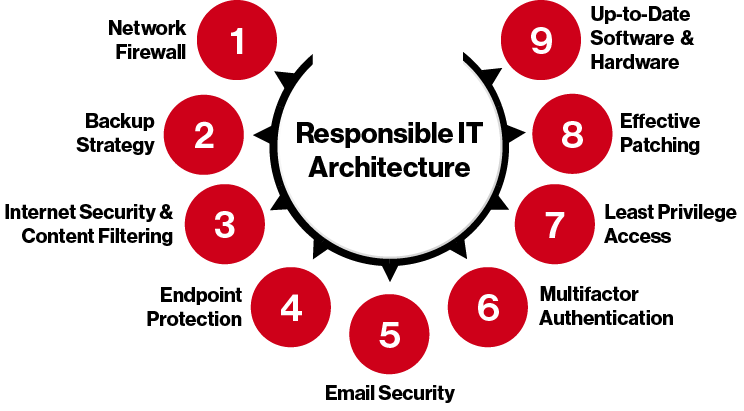
Least Privilege Access is a part of Responsible IT Architecture
There are nine tools that we use at Integris to help us ensure that the standards of a Responsible IT Architecture are met, and least privilege access is one of them.
When you work with us, we prefer to take a holistic security approach. For us, that means employing these nine pillar tools, working in tandem, to create a complete layer of protection around your systems. Whether all those tools come from us, or they are existing tools in your network, it’s important that they are updated, up to the standards of regulators/cyber insurers, and up to the security demands of your network.
We’ll work with you to make sure your systems work as intended, and we’ll provide the capacity to keep your company safe and productive.
Learn more about Least Privilege Access
Why Multifactor Authentication is Way Better Than Passwords
Learn how things like biometric scanning, location and possession factors can help keep your data safer than a password.
Multifactor Authentication Breakdown
We’re going through a full breakdown into MFA: how much it really protects you and your organization, the things to look out for when selecting a service, and more.
Multifactor Authentication: Worth The Cost?
Sorry for the clickbait title, but yes. Yes yes yes.




