Honestly…2020 has been a heck of a year. A pandemic, a recession, a contentious election, and then a hack that impacted not only 18,000 business but rocked our Federal Government to its core.
Luckily we’re not alone in this fight. Our partners, like (INSERT NAMES), have got our back and like the Infinity Stones from Marvel’s movie series, have supplied us with powerful tools to protect our customers.
So, if you’re not familiar with the Solar Winds hack, I included a link to a summary article above, I suggest reading that first to catch up before continuing. If you’re already caught up, we can continue and the rest of the class will join us by the time we start the next paragraph.
Everybody back with us? Great! Let’s continue. What you see below is taken directly from our partner websites with attribution links posted at the bottom of each section so you can follow along with their coverage directly.
Cybereason
The Cybereason Defense Platform provides multi-layered protection and is designed to block advanced threats like the SolarWinds Supply Chain attack at multiple points during the attack sequence. The following blog explains how our platform will block the attack based on the Indicators of Compromise (IOCs), but more importantly how it can also block the attack based on the more subtle Indicators of Behavior (IOBs).
The Cybereason Defense Platform is purpose-built to detect and prevent the most advanced attacks techniques, such as those leveraged in these recent attacks. When the malware attempts to initiate the Domain Generation Algorithm (DGA) stage to establish communications with the C2 servers, Cybereason recognizes this behavior as malicious and immediately blocks the threat.
Despite the fact that the malicious code appears to be part of a legitimate software update signed by a valid digital certificate, Cybereason recognizes the less obvious behaviors the code attempts to engage in and blocks it based on a deeper understanding of how Malops actually work, even if the threat is advanced enough to circumvent traditional signature AV and nextgen ML-based detections.
This capability is what makes the Cybereason Defense Platform truly future-ready: when attackers develop new techniques that evade other security solutions, Cybereason’s operation-centric approach and unparalleled visibility into complex Malops allows our solution to block threats at multiple stages of the attack and provide the most comprehensive endpoint prevention, detection and response on the market.
(Taken from: https://www.cybereason.com/blog/cybereason-vs-solarwinds-supply-chain-attack)
Fortinet
Over the past week, the FortiGuard Labs research teams have worked tirelessly to uncover more details on the attack to ensure our customers are protected, details of which can be found in our Threat Signal Blog. In this blog, we share more detail on what we have learned, the protections currently provided by products in our portfolio, as well as the proactive steps we have taken leveraging our FortiEDR platform to ensure the security of our customers.
Steps Fortinet is Taking to Ensure the Security of our Customers:
- All published and subsequent IOCs were immediately added to our Cloud intelligence and signatures databases to ensure detection of the malicious files by Fortinet’s security solutions, including FortiGate, FortiSIEM, FortiSandbox, FortiEDR, FortiAnalyzer, and FortiClient. As new IOCs are uncovered, they will also be immediately added to our databases.
- In order to reconstruct the attack and gain more insights and indicators, FortiGuard Labs research and intelligence teams started to hunt for more indicators based on the initially disclosed data. As part of this effort, we have discovered and analyzed a new variant of TEARDROP. In Figure 2, you can see this TEARDROP variant read the fake jpeg header and its main unpacking routine:
- We also proactively scanned our FortiEDR Cloud data lake for indicators to determine if customers may have been breached. Customers that were potentially impacted are being contacted.
- Our MDR and FortiEDR research teams have also devised tools that can help organizations understand the scope of a breach in case they have been impacted by this supply-chain attack. These tools are being shared with customers upon request. As mentioned, most organizations were not targeted, and understanding the scope of the breach is critical for determining follow-up steps.
(Taken from: https://www.fortinet.com/blog/threat-research/what-we-have-learned-so-far-about-the-sunburst-solarwinds-hack)
SumoLogic
Regarding this particular supply chain attack and the associated SUNBURST backdoor investigated by FireEye, we recommend for our customers to start with the Threat Intelligence application from the Sumo Logic app catalog. For more information about our Threat Intelligence application, you can learn more here.
The Threat Intel Quick Analysis app correlates CrowdStrike’s threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyberattacks. The Threat Intel Quick Analysis App scans selected logs for threats based on IP address, URL, domain, Hash 256, and email.
To install this application within your Sumo Logic environment, please visit this quick guide.
Utilizing IOC lists:
FireEye released a list of IOCs that were a part of the SolarWinds Orion SUNBURST supply chain attack.
You can easily search the IOCs across all of your data that is currently collected within Sumo Logic. Simply put the IOC name within the scope of your search query to locate relevant results against this IOC list.
Here is a sample query:
Loading IOC lists:
Another way of managing IOC lists within the Sumo Logic platform is by creating lookups. Sumo Logic supports lookup creation in two methods: 1.) Create a Lookup via the Sumo Logic UI, or 2.) Create a Lookup via Sumo Logic Lookup API. To learn more about creating lookups, please consult this guide.
Once a Lookup is created, based on the instructions above, you can run the Sumo Logic query against a particular IOC type within the Sumo Logic platform.
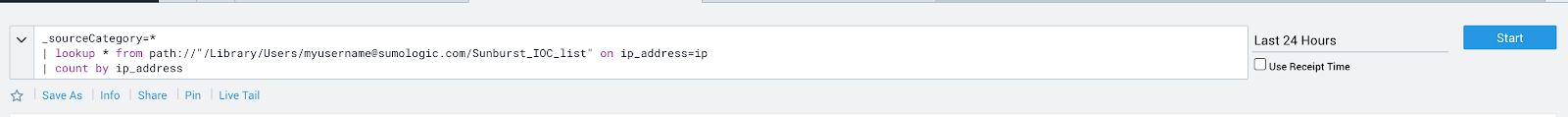
Example :
_sourceCategory=* | lookup * from path://”/Library/Users/[email protected]/Sunburst_IOC_list” on ip_address = ip | count by ip_address
The above query is specific to IP address type IOCs; this query can be modified to look for additional IOC types as well, including file hashes, domains, and more.
How to search available HTTP sources for SolarWinds indicators
The Sumo Logic SpecOps team recommends the following searches, based on FireEye’s SUNBURST Snort IDS rules, for outbound HTTP traffic to attacker-controlled domains. These searches assist with surfacing Command and Control (C2) traffic masquerading as SolarWinds Orion Improvement Program (OIP) traffic, as well as the FQDN observed in use by the attacker: avsvmcloud[.]com.
1. HTTP traffic to suspicious URI paths masquerading as SolarWinds traffic:
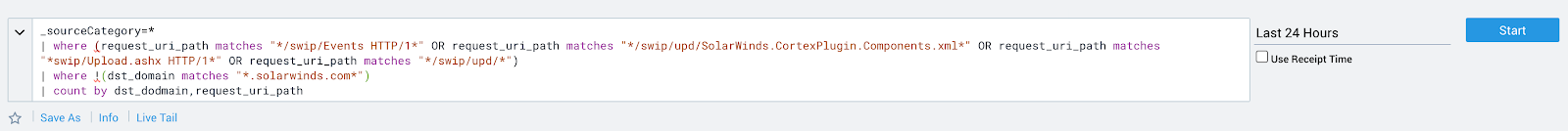
Example:
_sourceCategory=* | where (request_uri_path matches “*/swip/Events*” OR request_uri_path matches “*/swip/upd/SolarWinds.CortexPlugin.Components.xml*” OR request_uri_path matches “*swip/Upload.ashx*” OR request_uri_path matches “*/swip/upd/*”) |where !(dst_domain matches “*.solarwinds.com*”) | count by dst_domain, request_uri_path, ip_address
2. HTTP traffic going to the malicious domain of avsvmcloud[.]com:
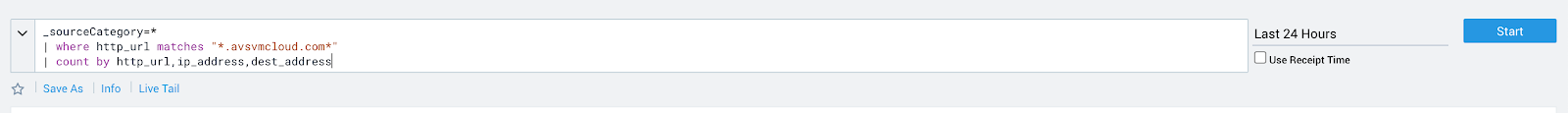
Example:
_sourceCategory=* | where http_url matches “*.avsvmcloud.com*” | count by http_url, ip_address, dest_address
(Taken from: https://www.sumologic.com/blog/monitoring-solarwinds-supply-chain-attack-with-cloud-siem/)
Zscaler
Zscaler Coverage
Zscaler leveraged the details on the countermeasures provided, verified that there is existing protection and enhanced the coverage wherever required across the multiple layers of Zscaler security platform. Below is the list of threat names through which Zscaler products detect this campaign.
Advanced Threat Protection
- Win32.Backdoor.SunBurst
- Win32.Backdoor.BEACON
Malware Protection
- PS.Trojan.COSMICGALE
- Win64.Dropper.TearDrop
- Win32.Webshell.SuperNova [attribution not confirmed]
- Win64.Trojan.TearDrop
Details regarding these threat signatures can be found in the Zscaler Threat Library.
Advanced Cloud Sandbox
We have ensured that Zscaler Cloud Sandbox flags the Sunburst Backdoor. As always, Cloud Sandbox plays a critical role in blocking any unknown variants of the malware.
Zscaler ThreatLabZ team is also actively monitoring this campaign and any activity around Sunburst Backdoor and will ensure coverage for newer IOCs as they are discovered.
Is Zscaler affected?
Zscaler utilizes SolarWinds software and verified that none of our services are affected by this campaign. We published a trust advisory here: https://trust.zscaler.com/posts/6896
Zscaler Platform Best Practices:
- Route all server traffic through Zscaler Internet Access, which will provide the right visibility to identify and stop malicious activity from compromised SolarWinds servers.
- Restrict traffic from critical infrastructure to an allow list of known-good destinations
- Ensure you are inspecting all SSL traffic.
- Turn on Advanced Threat Protection to block all known command-and-control domains.
- Extend command-and-control protection to all ports and protocols with the Advanced Cloud Firewall (Cloud IPS module), including emerging C2 destinations.
- Use Advanced Cloud Sandbox to prevent unknown malware delivered as part of a second stage payload.
- Limit the impact from a potential compromise by restricting lateral movement with identity-based micro-segmentation (Zscaler Workload Segmentation) and a Zero Trust architecture.
- Safeguard crown jewel applications by limiting lateral movement using Zscaler Private Access.
(Taken from: https://www.zscaler.com/blogs/security-research/zscaler-coverage-solarwinds-cyberattacks-and-fireeye-red-team-tools-theft)




