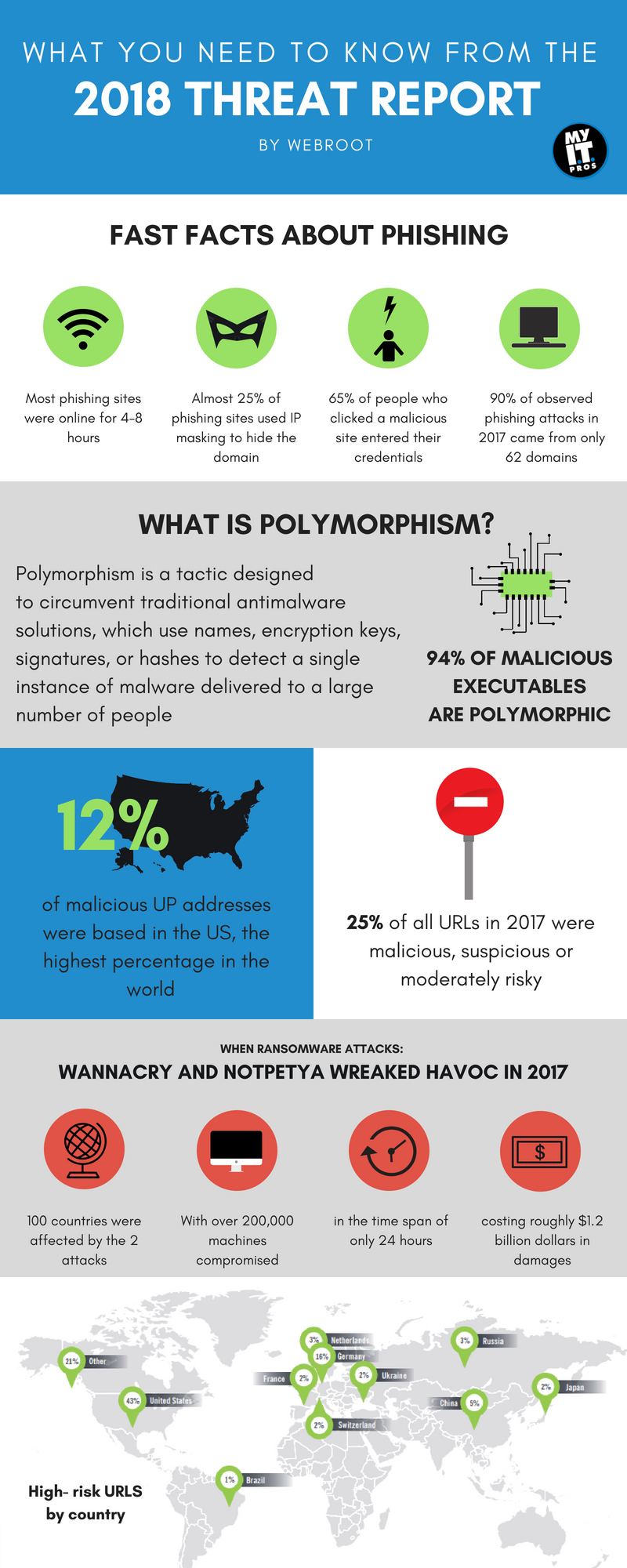
The 2018 edition of Webroot’s Threat Report shares a glimpse into the discoveries and analysis of threat activity throughout 2017. While the report covers everything from trends in polymorphism to malicious IP addresses to the danger of phishing attacks, check out some of the most interesting (in our opinion!) and important information below.