For years we’ve read articles teaching us to identify the signs an email is phishing. We all know the signs, yet we still miss the blatant indicators and take the bait.
According to Security Magazine, citing SlashNext, “The first six months of 2022 saw more than 255 million attacks — a 61% increase in the rate of phishing attacks compared to 2021.”
SlashNext analyzed billions of link-based URLs, attachments, and natural language messages in email, mobile and browser channels and published the findings in their State of Phishing 2022 whitepaper.
Statistics like this make me feel like everyone is continuously slipping on the same proverbial banana peel.
Since phishing is only getting worse, we’ll review five telltale indicators, critique recent examples, and share protective best practices to sharper your defenses against inbox intruders.
#1 – Bad Grammar is One of the Signs of Phishing
When threat actors in non-English speaking countries send phishing emails to millions of targets worldwide, bad grammar is a feature rather than a bug.
An Integris client recently submitted the following redacted support ticket to our MSP help desk.
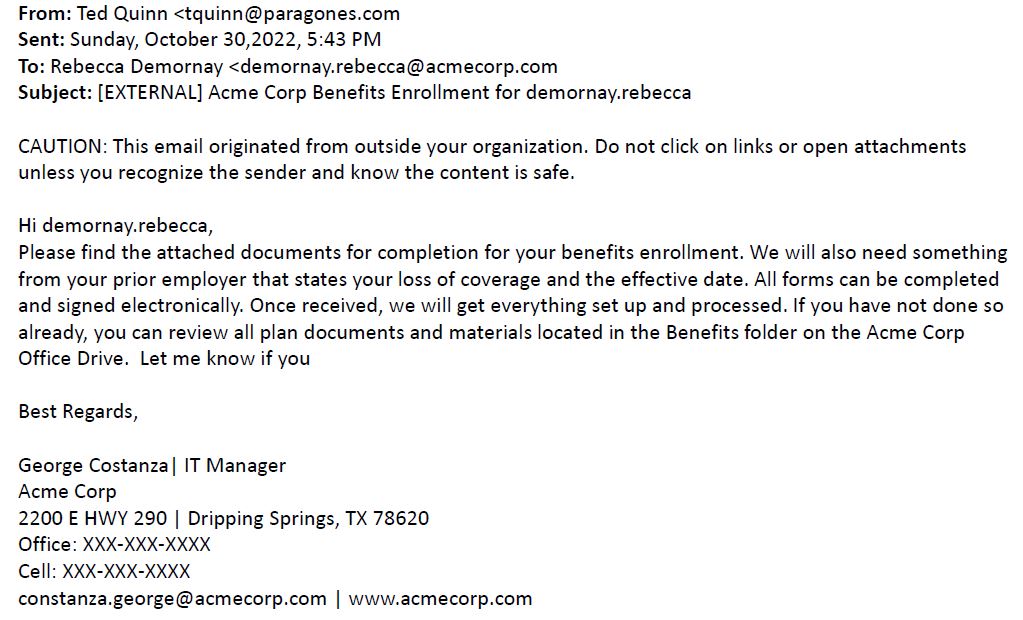
This sloppy communique raises several questions:
- Why is the sender, [email protected], not the same person, with the same email address, in the signature of the email?
- What’s going on with the final sentence? It just drops off into nowhere. Let me know if you…Really?
- Why is an IT Manager sending a benefits enrollment email? Isn’t HR responsible for managing benefits everywhere you’ve ever worked?
- I disguised the recipient’s real name, but it reads Hi, demornay.rebecca. Who sends lowercase greetings that begin with the last name? Cyberthieves who think they’re targeting people who sit around the office drinking craft cocktails all day?
Our client did the right thing by asking us to vet this egregious phishing email.
Please open a support ticket with your MSP whenever emails exhibit similar signs of phishing.
#2 – Signs of a Phishing Email Include @freewebmail Domains and Mismatched Sender Email Addresses
Hackers love sending phishing emails from Gmail accounts with different sender addresses and branding elements in plain view.
Expert Insights reports, “The biggest category of phishing, according to a study by APWG, is targeted towards webmail and Software-as-a-Service (SaaS) users; these types of attack are responsible for 34.7% of phishing attempts.”
“The same study reported an increase in the number of BEC attacks sent from free webmail providers, from 61% to a staggering 72%, and found that over half of these attacks used Gmail as their delivery method.”
This phishing email landed in my Yahoo account (just in time for this article). The sender purports to be Yahoo, yet they use a Gmail address. Wow, “Ronad Kat” – you almost got me!
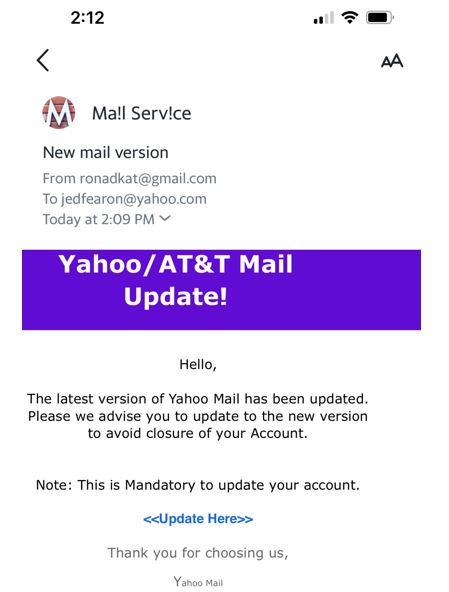
This feeble attempt at social engineering has several other signs of a phishing email clown show:
- The M logo paired with Ma!l Serv!ce looks random and doesn’t resemble anything I’ve ever received from Yahoo.
- Yahoo spells “Mail Service” without substituting exclamation points for actual letters.
- What’s up with the Yahoo/AT&T Mail connection? Did I miss their recent joint venture announcement? Sketchy!
- When has Yahoo ever threatened anybody with account closure for refusing to update their free email service hosted on Yahoo servers? Yahoo does the updates, so we don’t have to!
- “This is Mandatory to update your account” is too clunky to sound like it’s from Yahoo HQ. I’m sure they use Grammarly and would probably say, “This account update is mandatory.”
- The blue <<Update Here>> link is one step up from the “surprise” hand buzzer gag your great-grandfather has pestered you with every Thanksgiving since the Bush administration.
We cite this example because most of us access webmail accounts at work, which exposes corporate assets to email phishing schemes.
Here’s what to do when you receive suspicious emails via Yahoo and other free webmail services:
- Click on the checkbox to the left of the message
- Right-click your mouse or touchpad
- Select SPAM from the drop-down menu, and the offending message goes to the TRASH
#3 – Random Links and Attachments Are Obvious Signs an Email is Phishing
I’m so scared of attachments and their association with phishing I hesitate to open PDFs and Word documents from close colleagues.
The fear is justified because malicious senders can commandeer legitimate user accounts in M365 and assemble dead-ringer impersonations.
The imposter scam is easy to do by leveraging open-source intelligence from social media sites like Facebook and LinkedIn.
For instance, when threat actors see one of my educational videos on LinkedIn, they also see the names and faces of connections and work associates.
They can also view comments and study personal rapport to create context-rich, customized phishing campaigns.
While I have no plans to abandon LinkedIn, I’m always on high alert when I see subject lines with resume and cover letter attached or body copy with links that say click here to see samples of my work.
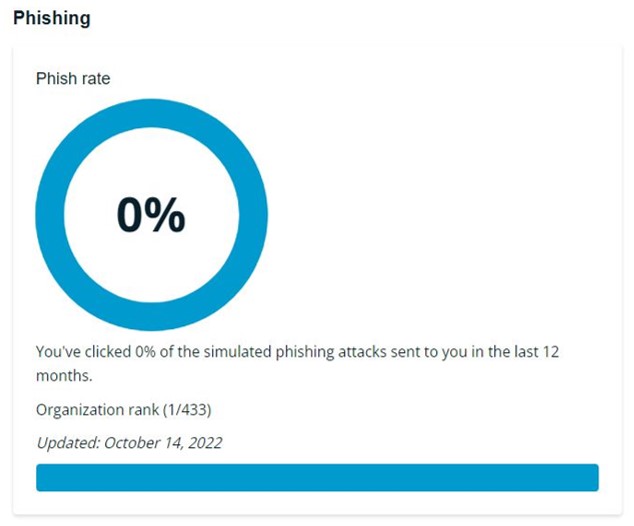
So far, I haven’t taken the bait. This distinction makes me grateful for Integris’ investment in monthly cybersecurity awareness training, including ethical phishing tests.
My latest report card reveals a zero-percent click rate over the last 12 months.
I recommend Cybersecurity Awareness Training to all businesses and anyone willing to listen.
#4 – Threatening Tones and Urgent Demands Are Signs of Phishing
Cybercriminals deliver threatening phishing emails that exploit everyone’s fear of financial consequences.
Crooks combine ingenious calls to action with captivating graphics and tempting links that give victims the perception of a quick fix.
The following “Bank of America” invoice won’t fool everyone. However, a minute percentage of several million people is a lucrative payday for a cyber cartel or hostile nation-state.
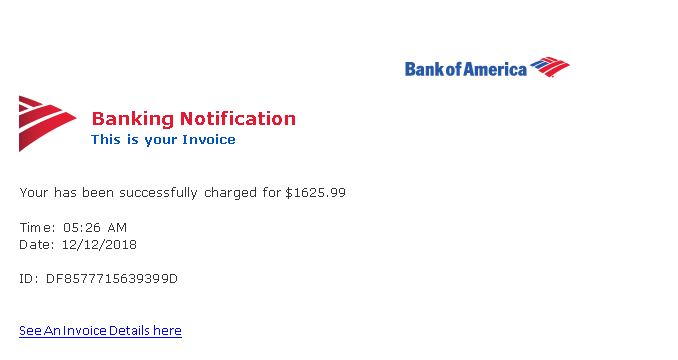
In the wrong frame of mind, the right person with a dozen other active tasks might panic and respond impulsively.
What? Is BOA zapping me for $1,625.99? I can’t wait to see this stupid invoice! (Then seconds after clicking) What was I thinking? I’m a Wells Fargo client!
Apple’s infamous account lock-out threat creates similar “fire, ready, aim” responses.
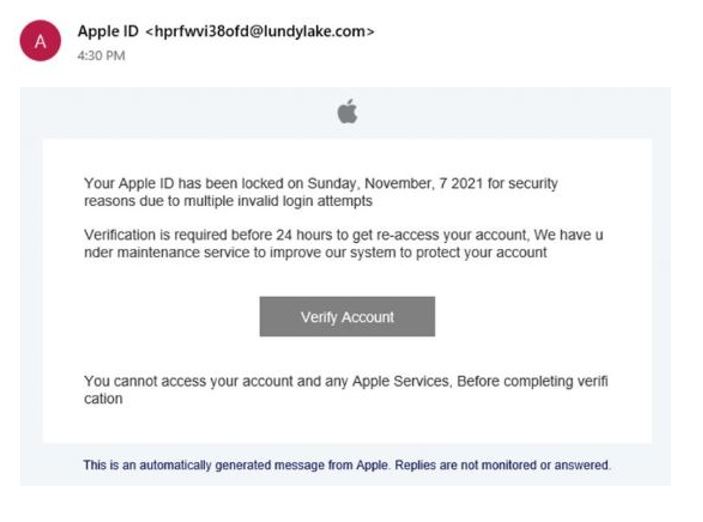
Since millions of people will respond without looking closer, victims will overlook overt signs of phishing:
- The sender’s address, [email protected], is bizarre.
- The verification directions are poorly punctuated and contain conspicuous diction like “to get re-access your account.”
- The Verify Account button is a ploy to collect user login credentials to access Apple Pay/credit card data.
When I receive messages like this, I follow the directions we shared in section 2.
I’ve also developed an all-new habit. Whenever I get something phishy from “PayPal” – which is all the time – I do quick Google searches to verify my suspicions.
And I always land on helpful articles that immediately confirm the validity of my skepticism. I hate to admit it, but it’s fun. I’m slightly competitive, and the exercise makes me feel like I’m winning against the bad guys.
Learn More: PayPal Invoice Phishing Scam and How to Spot a Fake PayPal Email
#5 – Dear Client Requests for Sensitive Information Are Signs an Email is Phishing
Dear Client greetings and requests for personal identifying information are almost always phishing emails.
Hello, Mr. Last Name, Hello, and Dear Customer are other red flags. This effort, masked as a verification exercise from QuickBooks, is shady.
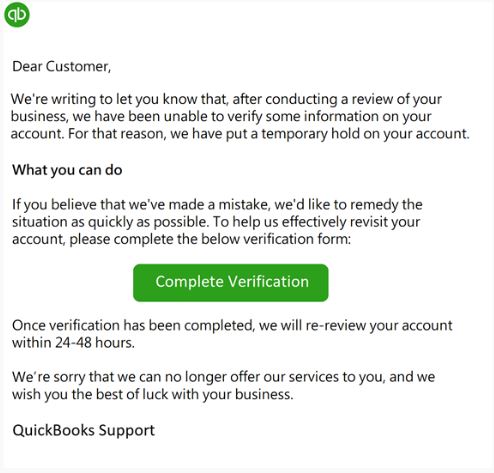
The pivot from Dear Customer to we have put a temporary hold on your account is swift and grave. And everyone knows disabling QuickBooks is synonymous with shutting down the central nervous system of a business.
I went through a brief refresher and reviewed recent emails from all my accounts. From Witch’s Rock Surf Camp to Wells Fargo, the greetings are personalized and customized to match the culture of the enterprise.
Some also use my formal name (Jared), which I’ve never seen in a phishing email:
- Hey there, Jed
- Hey Jed
- Hi Jared Fearon
- Hello Jared
- Dear Mr. Fearon
However, beware of the change-up pitch. This ploy happens when fraudsters shift to an overly informal address or start with a simple Hope you are well.
I expect Witch’s Rock Surf Camp to say, “Hey there, Jed. Hope you are well.” Conversely, the same greeting from Wells Fargo would create an instant pause because they’re a financial institution. It’s always Dear Mr. Fearon in everything they send me.
It’s advisable to stay on high alert because technical solutions don’t always detect obvious signs of phishing emails and all-new scams.
Learn More: A Personal Twist on Zero Trust Security
Do You Have a Partner for Your Phishing Email Reduction Journey?
Partnering with an MSP is one of the best ways to reduce phishing emails and related blowback.
The following mini-case study from Integris Sr. System Engineer Billy Everett has a happy ending and neatly summarizes simple changes that make a huge difference.
While working for another MSP about five years ago, we got a call first thing in the morning from a client. Ransomware had locked down all file shares and encrypted everything.
Thanks to records from their SIEM showing mass file encryptions pointing to a single user helped to identify the breach in the system.
We took the PC offline and brought it up to review browsing history, found the culprit of the matter to be from an employee checking their personal email and clicking on a classic UPS “your package has been delivered, click here to view the shipping receipt” to open a malicious PDF file.
After wiping the PC, we took measures to get the network back up and running. We restored the file shares as they were before the ransomware attack, thanks to hourly backups.
Several security issues allowed the attack to take place:
- At the time, there wasn’t any training for detecting phishing emails.
- The user was a local PC admin, allowing free reign to run the malicious software from the PDF.
- The antivirus was also lackluster and did not detect the file.
- File shares without proper permissions allowed the attack to spread through all folders, versus a mitigated attack of only the files the employee should have access to.
Our main point of contact had been warning upper management of how vulnerable the network was to attack, but we could not get the approval for improvements. After being down over a full business day, management approved the roll-out of additional security measures:
- All users, no exceptions, were no longer local administrators for their PCs.
- The antivirus was replaced with a far more robust Next-Gen one capable of detecting threats.
- All file shares were reviewed for proper permissions so users would only have access to the files deemed required for them.
- Management implemented phishing training for all employees.
Do your employees get monthly reminders like this? If not, it’s time to change that.

Schedule a Free Consultation if you have questions about phishing emails, cybersecurity awareness training, and information privacy.



