Back in the days before the term “CryptoLocker” existed, something called scareware was a favorite method of extorting computer users. As technology advanced, so did the means by which scareware is deployed. The IT good guys have gotten better at counteracting traditional viruses, prompting cybercriminals to revert back to the tried and true method of compromising the end user.
What is scareware?
Over the past few months, we’ve seen a resurgence of browser-based scareware. A few years ago, these types of infections more closely resembled traditional viruses – once activated, they would download a file and run when the computer booted, effectively locking you out of the system. As browser-based applications evolve, older technologies such as Flash and Java are updated less frequently, which makes them more exploitable as they are slowly phased out. Exploits that target these technologies take over the screen or create a popup that claims your computer has a major issue or is being attacked. Typically, a reboot is all that’s needed to clear up these one-time exploits.
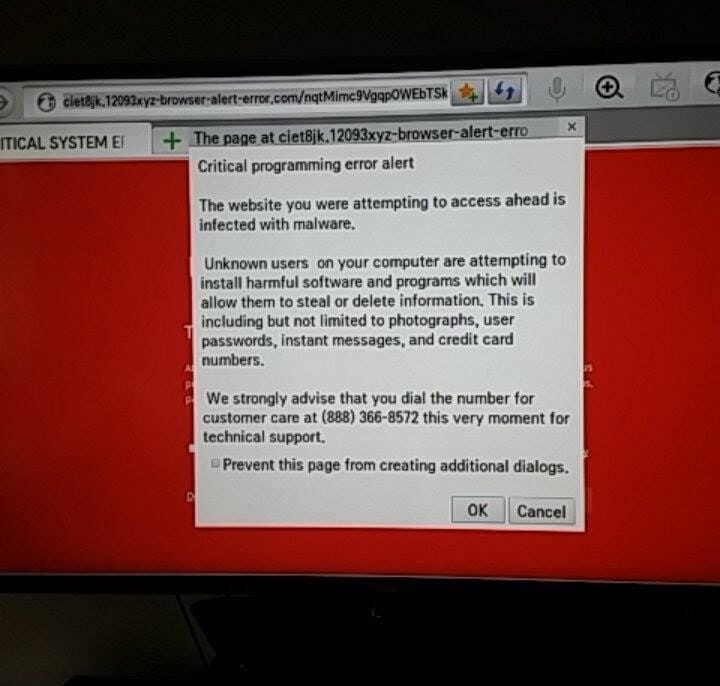
Meanwhile, the new browser scareware often relies on a method called malvertising. In this scenario, a website with an infected ad network uses a Java- or Flash-based exploit to launch malicious code. Because these technologies are browsers on all types of devices – even smart TVs, as shown here:
As you can see, this example of scareware is urging the user to call “technical support” for assistance. Once you’re on the phone, the “technician” will attempt to hijack your device by trying to sell you software that will only cause more issues and result in more support calls. Sometimes, these individuals will pretend to be from Microsoft or other well-known companies. In my experience, they can be very abrasive if questioned, but it’s a good idea to check out their credibility before authorizing access to your device.
How can I avoid it?
It is important to be vigilant and know what steps to take if anything questionable pops up on your computer. I once spoke to a user who encountered a popup that was blaring a warning message over his speakers – a major red flag that the message was not legitimate. He called the number provided, but after realizing the person on the other end of the line was up to no good, he disconnected (after using a few choice words!).
The bottom line is that scareware is typically harmless – unless you invite the perpetrators into your machine by engaging with malicious popups. Frequently updating your browser and browser plugins can help mitigate the risk, but you should also consider using an ad-blocking plugin on top of traditional antivirus solutions. Ad-blocking prevents compromised ad networks from loading on your machine, and helps speed up web browsing in the process. What’s more, it can be disabled on websites you trust, although it’s important to note that trusted sites can still be compromised. Ultimately, the best defense is understanding what is and isn’t normal when browsing the web, and knowing who to contact if something strange pops onto your screen.
 Nathan Mitten, Senior Systems Engineer
Nathan Mitten, Senior Systems Engineer
The goal of this blog is to answer the questions you ask! For more information about scareware and our anti-virus and anti-malware capabilities, feel free to contact me! Check out some more cyber security stats and information with this free infographic.